Accelerate HIPAA Compliance Using Databunker Pro
The following document provides an overview of key technical requirements for HIPAA compliance, including specific security controls and best practices for protecting personal health information (PHI). It identifies the relevant stakeholders, explains the requirements, and shows how Databunker Pro helps meet these standards. By leveraging Databunker Pro’s features—such as secure storage and encryption of personal data (PHI), access controls, multi-tenancy, secure bulk retrieval, consent management, credit card tokenization, and audit logging—organizations can protect personal data and ensure compliance with the HIPAA standard.
HIPAA Technical Requirments
| Title | Stakeholders | Description | How Databunker Pro Can Help |
|---|---|---|---|
| Access Control (164.312(a)(1)) | IT, Security teams | Implement unique user IDs, emergency access procedures, and automatic session terminations. | Databunker Pro provides robust access control mechanisms, supports multi-tenancy, and ensures granular permission enforcement, enhancing HIPAA compliance for diverse organizational setups. |
| Audit Controls (164.312(b)) | IT, Security, Developers | Record and monitor access to protected health information (PHI). | Logs all access and modifications to sensitive data with detailed timestamps for compliance audits. View security guide. |
| Data Integrity (164.312(c)(1)) | Developers, IT, Security | Protect PHI from improper alteration or destruction. | Databunker Pro ensures data integrity with encryption, access controls, and strict multi-tenancy, reducing the risk of tampering or unauthorized modifications. |
| Encryption and Decryption (164.312(a)(2)(iv)) | IT, Developers | Encrypt PHI during transmission and storage. | Databunker Pro acts as an encrypted vault, securely storing PHI and encrypting data at rest and in transit. It also supports encryption key rotation to comply with strict security regulations. |
| Person or Entity Authentication (164.312(d)) | Security, Developers | Verify the identity of individuals accessing PHI. | Databunker Pro integrates with authentication systems, providing secure user authentication to protect access to PHI. |
| Workstation Security (164.310(b)) | IT, Security | Implement physical safeguards to restrict access to workstations containing PHI. | Databunker Pro stores helth data centrally in an encrypted vault with strict access controls. This reduces the risk of sensitive data being stored locally on a workstation, which could be lost or stolen. |
| Transmission Security (164.312(e)(1)) | IT, Security, Developers | Protect PHI against unauthorized access during transmission. | Databunker Pro encrypts PHI during transmission and supports secure bulk retrieval, ensuring safe and efficient data transfers. |
| Security Incident Procedures (164.308(a)(6)) | Security, IT, Compliance | Implement procedures to identify, respond to, and document security incidents. | Databunker Pro’s detailed audit trails and logging help organizations investigate and document security incidents effectively. |
| Contingency Plan (164.308(a)(7)) | IT, Security | Establish policies and procedures for emergency operations to protect PHI. | Databunker Pro supports encrypted automatic backups, helping ensure data availability and fast recovery during critical events. |
| Breach Notification (164.404) | Compliance, Security | Notify affected individuals and authorities of data breaches promptly. | Databunker logs access and modifications, providing forensic data to identify the scope of a breach and support notifications. |
| Physical Safeguards (164.310(a)(1)) | IT, Security | Implement physical access controls for facilities housing PHI. | Databunker Pro reduces physical risks by centralizing ePHI in a secure vault, avoiding local storage on workstations or portable devices. |
| Facility Access Controls (164.310(a)(1)) | IT, Security | Implement policies to limit physical access to systems containing PHI. | Databunker Pro centralizes ePHI in a secure vault, reducing reliance on physical workstations or on-prem servers and limiting physical access risks. |
| Device and Media Controls (164.310(d)(1)) | IT, Security | Implement policies for the disposal, reuse, and backup of devices containing PHI. | By avoiding local storage, Databunker Pro minimizes risks tied to device loss, reuse, or improper disposal. |
| Risk Analysis (164.308(a)(1)(ii)(A)) | IT, Security, Compliance | Conduct an accurate and thorough assessment of risks to PHI. | Databunker Pro assists in securing PHI, reducing risks identified during assessments. |
| Risk Management (164.308(a)(1)(ii)(B)) | IT, Security | Implement security measures to mitigate identified risks to PHI. | Databunker Pro provides encryption, access control, secure bulk retrieval, and auditing tools to mitigate risks effectively. |
| Training and Awareness (164.308(a)(5)) | Security, Compliance | Provide security training to all workforce members handling PHI. | Databunker Pro includes training on secure product usage and best practices for handling health data, supporting HIPAA awareness requirements. |
| Business Associate Agreements (164.308(b)(1)) | Compliance | Ensure that all business associates comply with HIPAA regulations. | With Databunker Pro, customers retain full control over their ePHI storage and compliance, with our support during the initial configuration to align with HIPAA best practices. |
| HIPAA Privacy Rule - Individual Rights (164.524) | Compliance, IT, Developers | Ensure individuals can access, request, and amend their PHI records. | Databunker Pro’s user interface supports individual rights by enabling access, updates, and corrections to PHI records. |
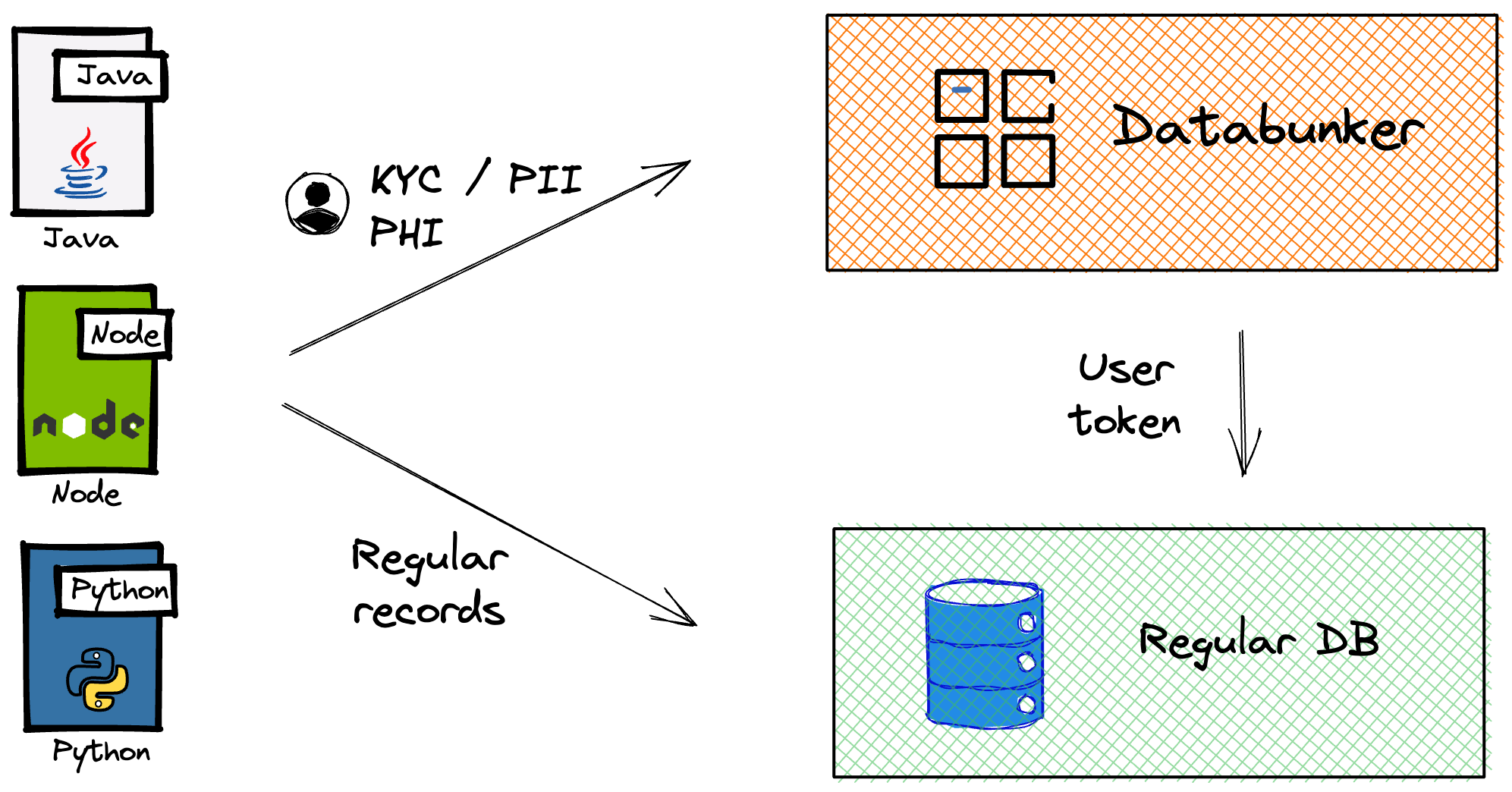
Conclusion:
By leveraging Databunker Pro’s comprehensive features, organizations can bolster their HIPAA compliance efforts, instilling confidence in patients and stakeholders alike. Embrace the power of open-source Databunker to safeguard PHI and ensure the highest standards of privacy and security within your healthcare environment.
👋 Want to learn about Databunker?
Take a closer look at how Databunker securely stores and manages sensitive data at scale.
