DPDPA Compliance Checklist for Startup Superheroes
Originally launched as an open-source project, Databunker has grown into a powerful, secure database solution designed to empower startups tackling the challenges of consumer data security.
In this document, we break down the technical requirements and security controls needed to comply with India’s Digital Personal Data Protection (DPDP) Act. We identify the key stakeholders, explain the core obligations, and show how Databunker Pro can help you get there faster.
With built-in support for secure storage and encryption of personal data (PII, PHI, KYC records), access controls, multi-tenancy, secure bulk data handling, consent management, credit card tokenization, and detailed audit logging, Databunker Pro helps you stay compliant and secure—without the overhead.
Table 1: Obligations of Data Fiduciaries
| Title | Stakeholder | Description | How Databunker Pro Can Help |
|---|---|---|---|
| Obtain Consent Section 5(1) |
Compliance, Developers | Ensure explicit consent is obtained from data principals before processing data. | Databunker Pro has a consent management capability, allowing organizations to store and manage user consent. |
| Purpose Limitation Section 6(1) |
Developers, Compliance | Process data solely for the purposes specified at the time of collection. | Databunker Pro’s detailed audit trails and logging can help organizations to tracks and limits data use. |
| Data Minimization Section 4(a) |
Developers, Compliance | Collect only the data that is necessary for the specified purpose. | Databunker Pro offers a unique data expiration policy that automatically deletes personal records no longer in use. Additionally, it includes a specialized API for credit card deduplication. |
| Data Breach Notification Section 8(5) |
Compliance, Security | Notify the Data Protection Board and affected data principals about breaches. | Databunker logs access and modifications, providing forensic data to identify the scope of a breach. |
| Data Retention Section 7(2) |
Compliance, Developers | Retain personal data only for as long as necessary for the purpose. | Databunker Pro offers a unique data expiration policy that automatically removes personal records that are no longer in use. |
| Document processing activities Section 6(5) |
Compliance, Developers | Maintain documentation of data processing activities. | Databunker Pro provides detailed logs and audit trails to monitor data access and changes. |
Table 2: Security Controls and Safeguards
| Title | Stakeholder | Description | How Databunker Pro Can Help |
|---|---|---|---|
| Firewalls and IDS | IT, Security | Monitor and control incoming and outgoing network traffic. | Databunker Pro is neither a network firewall nor an IDS. It is a specialized data security solution that provides robust access control mechanisms, secure bulk retrieval and a wide range of additional data security features. |
| Data Encryption | Security, IT | Encrypt data at rest and in transit to prevent unauthorized access. | Databunker Pro acts as an encrypted vault, securely storing PHI and encrypting data at rest and in transit. It also supports encryption key rotation to comply with strict security regulations. |
| Access Controls | IT, Security | Ensure that only authorized personnel have access to personal data. | Databunker Pro provides robust access control mechanisms, supports multi-tenancy, secure bulk retrieval, and ensures granular permission enforcement, enhancing DPDP Act compliance for diverse organizational setups. |
| Regular Audits | Compliance, Security | Conduct regular assessments of security measures and identify vulnerabilities. | Databunker Pro provides detailed logging and auditing of access and data changes. |
| Incident Response Plan | Security, IT | Establish a response plan for data breaches and security incidents. | Databunker Pro’s detailed audit trails and logging can be a part of the organization incident response plan. |
| Employee Training | HR, Compliance | Educate staff on data protection principles and security protocols. | Databunker Pro includes training on secure product usage and best practices for handling health data, supporting training requirements. |
Table 3: Rights of Data Principals
| Title | Stakeholder | Description | How Databunker Pro Can Help |
|---|---|---|---|
| Right to Access Section 12(1) |
Compliance, IT Teams | Allow data principals to confirm if their data is being processed and access it. | Databunker Pro has a built-in customer portal that allows individuals (data subjects) to view and execute their rights. |
| Right to Correction Section 12(2) |
Compliance, IT Teams | Enable data principals to correct inaccurate or misleading personal data. | Databunker Pro has a customer portal where users can update their personal records. Admin approval may be required. |
| Right to Erasure Section 12(3) |
Compliance, IT Teams | Permit data principals to request deletion of personal data no longer necessary. | Databunker Pro has a forget-me operation that allows users to request personal data deletion. |
| Right to Portability Section 12(4) |
Compliance, IT Teams | Provide data principals with their data in a structured, commonly used format. | Databunker Pro enables organizations to generate personal data reports, providing seamless support for data portability. |
| Right to Withdraw Consent Section 5(6) |
Compliance, IT Teams | Allow data principals to withdraw consent for data processing at any time. | Databunker Pro has a consent management capability, allowing users to withdraw their consent. |
| Right to Grievance Redressal Section 9 |
Compliance | Provide mechanisms for data principals to seek redressal for grievances related to data processing. | Databunker Pro supports DPDPA compliance by ensuring secure data access, maintaining audit trails, and minimizing grievances. |
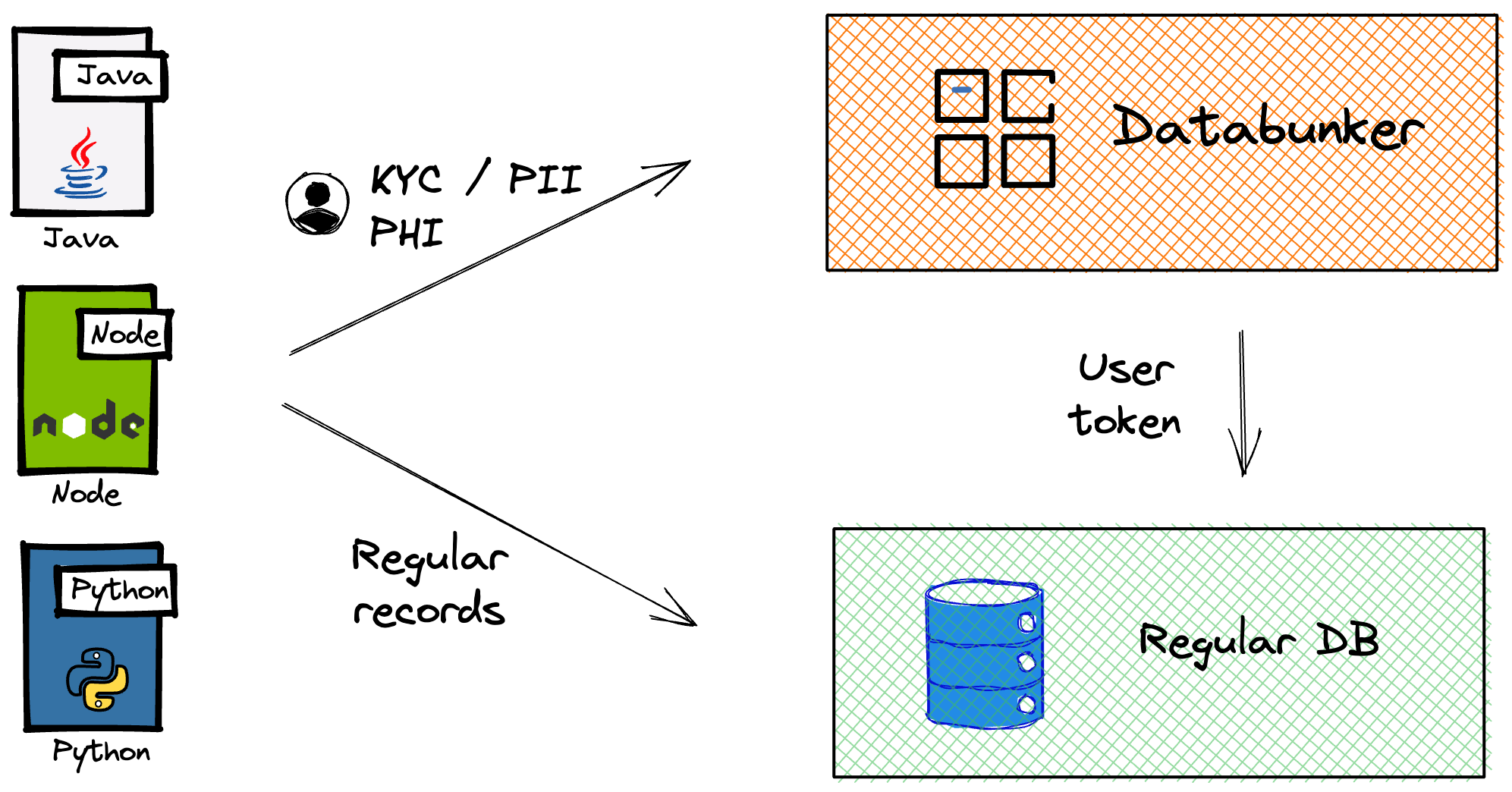
Conclusion
By adopting Databunker Pro, organizations can address the critical technical requirements of DPDP Act and implement best practices for secure data management. With its robust security controls, user rights management, and detailed audit capabilities, Databunker Pro empowers organizations to achieve DPDP Act compliance efficiently. Embrace Databunker Pro to protect personal data and ensure adherence to DPDP Act standards.
👋 Want to learn about Databunker?
Take a closer look at how Databunker securely stores and manages sensitive data at scale.
