Accelerate SOC2 Compliance with Databunker Pro
In today’s digital landscape, SOC2 compliance is a critical benchmark for organizations handling sensitive customer data. Developed by the American Institute of CPAs (AICPA), SOC2 (System and Organization Controls 2) evaluates an organization’s ability to meet five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. Achieving SOC2 compliance demonstrates a commitment to data protection, fostering trust with clients and partners. Databunker Pro, a secure vault for sensitive data, accelerates SOC2 compliance by providing enterprise-grade tools to safeguard personally identifiable information (PII), streamline security processes, and ensure audit-ready controls.
Why SOC2 Compliance Matters
SOC2 compliance is essential for technology and service organizations, particularly those managing customer data for SaaS, cloud, or fintech applications. It assures clients that robust controls are in place to protect data and maintain operational integrity. Non-compliance can lead to lost business, reputational damage, or regulatory penalties. Whether you’re a startup or an enterprise, Databunker Pro’s security-by-design approach simplifies SOC2 compliance, enabling you to meet client expectations and pass audits with confidence.
How Databunker Pro Helps with Relevant SOC 2 Trust Services Criteria
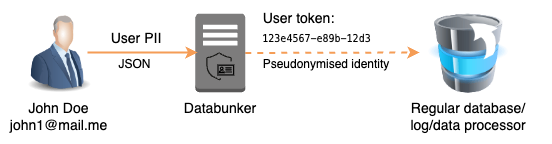
Databunker Pro is a secure vault designed to store sensitive records (such as PII, PHI, KYC data, and credit card information) with features like military-grade tokenization, AES-256 encryption (FIPS 140-2 compliant), role-based access controls (RBAC), comprehensive audit logs, user privacy portals, consent management, automated data minimization, encryption key rotation, and flexible deployment options (e.g., on-premises, Docker Compose, Kubernetes/Helm charts with sharding and horizontal scaling). These align with the AICPA’s 2017 Trust Services Criteria for SOC 2, supporting the five categories: Security (mandatory), Availability, Processing Integrity, Confidentiality, and Privacy (optional).
Security (Common Criteria)
This category is mandatory for SOC 2 and focuses on protecting systems against unauthorized access and damage. Databunker Pro supports several subcategories through its security-focused architecture.
-
CC6.0 Logical and Physical Access Controls: Enforces RBAC for granular permissions, API-only access (eliminating SQL/NoSQL/GraphQL injection risks), AES-256 encryption at rest and in transit (SSL), and token-based authentication to ensure only authorized access.
-
CC7.0 System Operations: Comprehensive audit logs track all API requests, accesses, modifications, and deletions (with PII in logs encrypted). Supports monitoring anomalies, incident response, and automated key rotation for operational integrity.
-
CC3.0 / CC7.0 Monitoring and Audit Logging: Generates detailed, encrypted audit trails for continuous monitoring, compliance reporting, incident investigations, and auditor evidence.
-
CC9.0 Risk Mitigation: Tokenization and data minimization reduce breach impact (real data never exposed externally), supporting vendor risk management and overall threat reduction.
Availability
This optional category ensures systems are operational and resilient. Databunker Pro’s deployment options make it relevant here.
-
A1.1 Current Processing Capacity: Scalable design handles 20M+ records with horizontal scaling (Kubernetes), database sharding, and stateless architecture for high availability.
-
A1.2 Environmental Protections: On-premises or region-specific deployments, backup features (e.g., Shamir’s Secret Sharing for master key recovery), and disaster recovery support protect against disruptions.
Processing Integrity
This optional category verifies accurate and complete data processing. Databunker Pro’s validation tools apply.
-
PI1.2 System Inputs: Built-in data validation, schema enforcement, and error-checking for inputs (e.g., PII/PHI fields) to ensure completeness and accuracy.
-
PI1.3 System Processing: Automated tokenization, hashing, and workflows maintain integrity during processing, with record versioning for change tracking.
-
PI1.5 System Outputs: Secure APIs for outputs (e.g., tokenized or masked data) ensure accurate, timely delivery while minimizing exposure.
Confidentiality
This optional category protects confidential information. Databunker Pro’s core tokenization is highly relevant.
-
C1.1 Identifies and Maintains Confidential Information: Tokenization replaces sensitive data (e.g., credit cards, PII) with tokens, while encryption and access controls identify and safeguard confidential assets throughout their lifecycle.
-
C1.2 Disposes of Confidential Information: Automated “forget-me” operations, data minimization APIs, and retention policies enable secure, timely disposal of expired/unnecessary data.
Privacy
This optional category manages personal information handling. Databunker Pro’s privacy tools directly support user rights and consent.
-
P4.0 Use, Retention, and Disposal: Consent management platform tracks preferences transparently; automated retention/disposal and data minimization enforce policies.
-
P5.0 Access: Optional User Privacy Portal provides passwordless access (email/SMS one-time codes) for data subjects to view, correct, update, or request data securely.
-
P6.0 Disclosure and Notification: Audit logs track disclosures; automation for data subject requests supports notifications and breach-related obligations.
-
P8.0 Monitoring and Enforcement: DPO tools offer oversight of audit trails, user request management, compliance reporting, and risk mitigation for ongoing enforcement.
Additional supporting features include secure hash-based indexing (no cleartext storage), record expiration, multi-tenancy isolation, and integration APIs for bulk operations. These mappings show how Databunker Pro automates many controls, provides auditor-ready evidence (logs, reports), and reduces compliance scope/effort. Not all subcategories are covered—only those with clear direct assistance. For a complete SOC 2 audit tailored to your organization, consult a professional auditor. Databunker also supports related standards like GDPR, HIPAA, PCI DSS, and ISO 27001.
User Request Automation
SOC2’s Privacy criterion emphasizes efficient handling of user data requests. Databunker Pro automates these processes through its User Privacy Portal, reducing administrative overhead. Supported user data management processes include:
- Data Access: Users can securely view their stored data.
- Data Deletion: The “forget-me” feature automates permanent data removal.
- Data Correction: Users can update inaccurate data via the portal.
- Consent Management: Automated tracking ensures compliance with user preferences.
These capabilities streamline SOC2 compliance by ensuring user data is managed securely and transparently.
DPO Management Capabilities
Data Protection Officers (DPOs) or security officers overseeing SOC2 compliance benefit from Databunker Pro’s robust tools. Key features include:
- Audit Trail Oversight: Detailed logs enable DPOs to monitor control effectiveness and prepare for SOC2 audits.
- User Request Management: The User Privacy Portal automates data subject requests, reducing operational burdens.
- Compliance Reporting: Databunker’s reporting tools generate evidence of Trust Services Criteria adherence.
- Risk Mitigation: Encryption and tokenization minimize breach risks, supporting DPOs in maintaining secure systems.
These tools empower DPOs to focus on strategic compliance while Databunker Pro handles operational controls.
Databunker Pro for Developers
Databunker Pro is built for developers, offering APIs and features to integrate secure data management into applications. Developer-focused capabilities include:
- API-Driven Integration: A RESTful API enables seamless storage and retrieval of sensitive data.
- Granular Access Control: Role-based access ensures only authorized users or applications interact with data.
- PII, PHI, and KYC Storage: Securely manage sensitive data types with built-in compliance.
- Credit Card Tokenization: Tokenize payment data to meet SOC2 and PCI DSS standards.
- Secure Bulk Requests: Process large-scale operations with encryption and access controls.
Developers can deploy Databunker Pro using Docker Compose or Helm charts, accelerating secure development and compliance.
Benefits of Using Databunker Pro
- Accelerated Compliance: Simplify SOC2, GDPR, ISO 27001, and HIPAA compliance with integrated security tools.
- Cost-Effective: Try enterprise features with a free 14-day trial—no credit card required.
- Flexible Deployment: Deploy on-premises or in the cloud, tailored to your infrastructure.
- Developer-Friendly: APIs and access controls enable rapid, secure integration.

👋 Want to learn about Databunker?
Take a closer look at how Databunker securely stores and manages sensitive data at scale.
