Accelerate ISO 27001 Compliance with Databunker Pro
In an era of rising cyber threats, achieving ISO 27001 compliance is essential for organizations aiming to establish a robust information security management system (ISMS). ISO 27001, a globally recognized standard, outlines requirements for protecting sensitive data, managing risks, and ensuring business continuity. Non-compliance can lead to reputational damage, financial losses, and regulatory scrutiny. Databunker Pro, a secure vault for sensitive data, accelerates ISO 27001 compliance by providing enterprise-grade tools to safeguard personally identifiable information (PII), streamline security processes, and demonstrate adherence to the standard.
Why ISO 27001 Compliance Matters
ISO 27001 certification demonstrates an organization’s commitment to information security, fostering trust with customers, partners, and regulators. Applicable to businesses of all sizes, it requires implementing controls to identify risks, secure data, and maintain detailed records of security practices. For startups and enterprises handling sensitive data, ISO 27001 compliance is a competitive advantage. Databunker Pro’s security-by-design approach simplifies the journey to certification, reducing complexity and ensuring alignment with ISO 27001’s rigorous standards.
How Databunker Pro Supports ISO 27001 Compliance
Databunker Pro is a lightning-fast, Go-based service designed to securely store sensitive records, such as PII, protected health information (PHI), know-your-customer (KYC) data, and credit card information. Its features map directly to ISO 27001’s Annex A controls and clauses, enabling organizations to build a compliant ISMS efficiently.
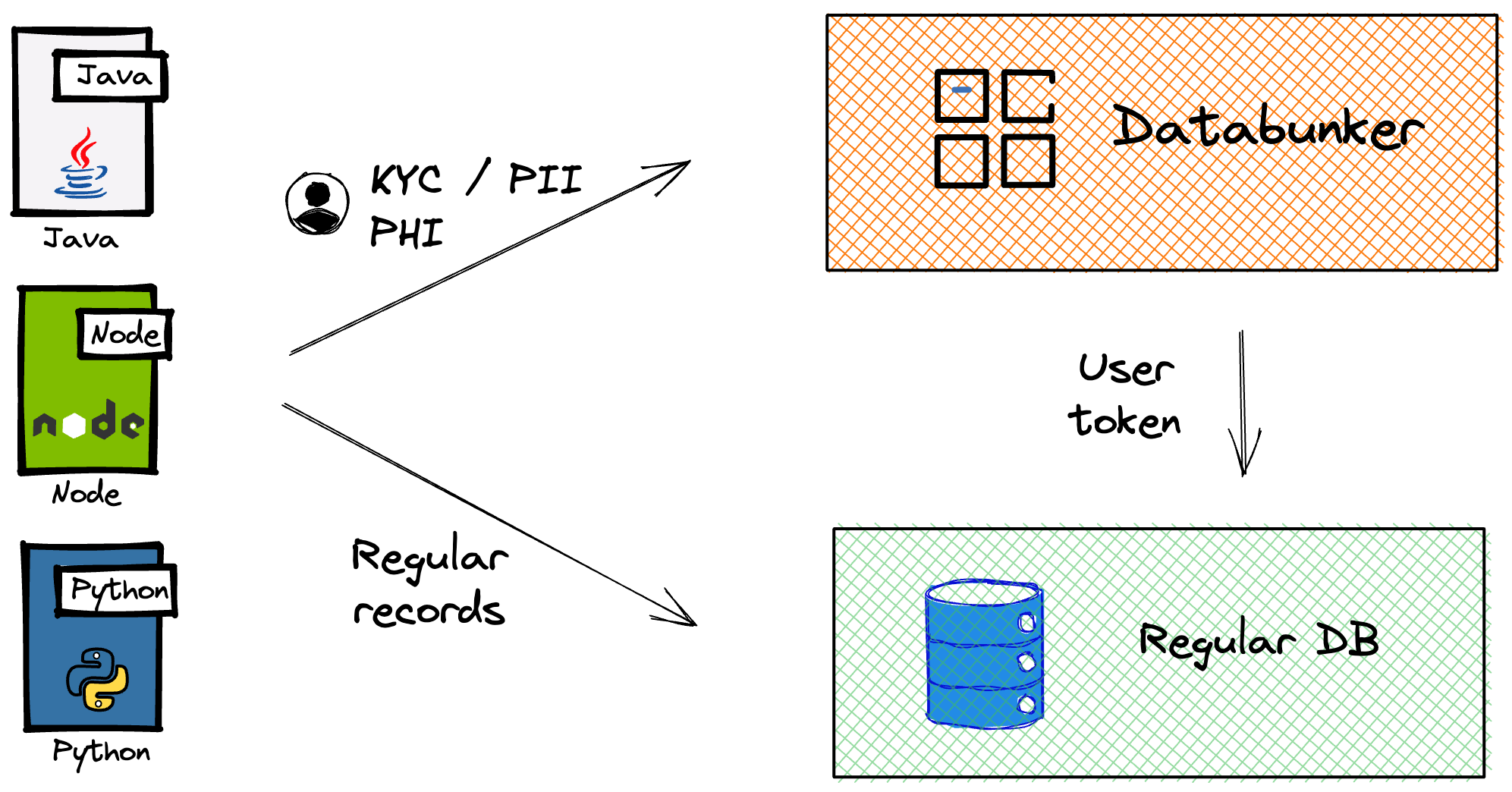
Secure Data Storage and Access Control
ISO 27001 (A.8.2, A.9.1) mandates protecting sensitive data from unauthorized access. Databunker Pro acts as an encrypted vault, using AES-256 encryption for data at rest and in transit. Its API-based access prevents SQL or GraphQL injection attacks, ensuring the confidentiality and integrity of PII, PHI, KYC records, and tokenized credit card details. Role-based access controls (RBAC) restrict data access to authorized users, aligning with ISO 27001’s access management requirements.
Risk Management and Incident Response
ISO 27001 (A.12.4, A.16) emphasizes identifying and mitigating security risks. Databunker Pro supports risk assessments by tokenizing sensitive data, reducing the impact of potential breaches. Its comprehensive audit logs enable real-time monitoring of data access and modifications, facilitating incident detection and response. By minimizing the attack surface through encryption and restricted data retrieval, Databunker helps organizations meet ISO 27001’s risk management obligations.
Audit Logging and Monitoring
Continuous monitoring and auditing (A.12.4) are core to ISO 27001 compliance. Databunker Pro generates detailed audit trails for all operations, tracking who accessed what data and when. These logs support internal audits, compliance reporting, and investigations, ensuring transparency and accountability. Automated logging reduces manual effort, helping organizations demonstrate adherence to ISO 27001’s monitoring requirements.
Policy Enforcement and Documentation
ISO 27001 (A.5.1, A.18.1) requires documented security policies and procedures. Databunker Pro’s built-in features, such as consent management and data minimization APIs, enforce security policies automatically. For example, the “forget-me” operation ensures timely data deletion, aligning with retention policies. Comprehensive documentation of Databunker’s security controls supports ISMS audits, streamlining certification processes.
User Request Automation
ISO 27001 (A.9.2) emphasizes managing user access and data subject requests securely. Databunker Pro automates user data management through its User Privacy Portal, enabling organizations to handle requests efficiently. Supported processes include:
- Access Management: Users can securely view their data via passwordless authentication.
- Data Deletion: The “forget-me” feature automates permanent data removal.
- Data Updates: Users can correct inaccurate data through the portal.
- Consent Tracking: Automated consent management ensures compliance with security policies.
These capabilities reduce administrative burdens and align with ISO 27001’s user access control requirements.
DPO Management Capabilities
Data Protection Officers (DPOs) or security officers overseeing ISO 27001 compliance benefit from Databunker Pro’s robust tools. Key features include:
- Audit Trail Oversight: Detailed logs enable DPOs to monitor ISMS performance and respond to security incidents.
- Automated User Request Handling: The User Privacy Portal streamlines data subject requests, freeing DPOs for strategic tasks.
- Compliance Documentation: Databunker’s reporting tools generate evidence of security controls, simplifying ISMS audits.
- Risk Reduction: Encryption and tokenization minimize data breach risks, supporting DPOs in maintaining a secure environment.
These tools empower DPOs to focus on ISMS governance while Databunker Pro handles operational security tasks.
Databunker Pro for Developers
Databunker Pro is designed for developers, offering APIs and features to integrate secure data management into applications. Developer-focused capabilities include:
- API-Driven Integration: A RESTful API enables seamless storage and retrieval of sensitive data.
- Granular Access Control: Role-based access ensures only authorized users or applications interact with data.
- PII, PHI, and KYC Storage: Securely manage sensitive data types with built-in compliance.
- Credit Card Tokenization: Tokenize payment data to meet ISO 27001 and PCI DSS standards.
- Secure Bulk Requests: Process large-scale operations with encryption and access controls.
Developers can deploy Databunker Pro using Docker Compose or Helm charts, accelerating secure development and compliance.
Benefits of Using Databunker Pro
- Accelerated Compliance: Simplify ISO 27001, GDPR, HIPAA, and SOC2 compliance with integrated security tools.
- Cost-Effective: Try enterprise features with a free 14-day trial—no credit card required.
- Flexible Deployment: Deploy on-premises or in the cloud, tailored to your infrastructure.
- Developer-Friendly: APIs and access controls enable rapid, secure integration.
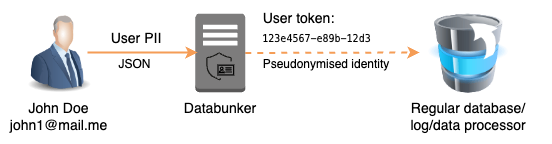
👋 Want to learn about Databunker?
Take a closer look at how Databunker securely stores and manages sensitive data at scale.
