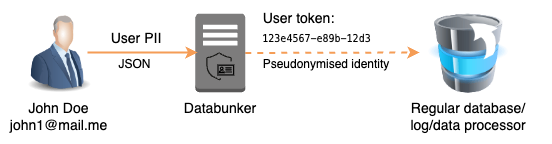
Databunker is an open-source, Go-based tool for secure personal data tokenization and storage. It can be deployed using Docker Compose or a Kubernetes Helm chart and is designed to help developers protect sensitive data such as PII, PHI, and KYC with minimal effort.
💣 The Big Problem with Traditional Database Encryption
Traditional database encryption solutions often provide a false sense of security. While they may encrypt data at rest, they leave critical vulnerabilities:
- Encryption alone isn’t enough: Most vendors offer disk-block encryption, ignoring API-level encryption
- Vulnerable GraphQL Queries: Unfiltered queries can expose unencrypted data to attackers
- SQL Injection Risks: Attackers can retrieve plaintext data through SQL injections
Databunker addresses these gaps with a secure, developer-focused solution for personal data tokenization and storage.
🛠️ Databunker Features
- Tokenization Engine: Generates UUID tokens for safe data referencing in applications
- Encrypted Storage: Secures sensitive records with advanced encryption layer
- Injection Protection: Blocks SQL and GraphQL injection attacks by design
- Secure Indexing: Uses hash-based indexing for search queries
- No Plaintext Storage: Ensures all data is encrypted at rest
- Restricted Bulk Retrieval: Disabled by default to prevent data leaks
- API-Based Access: Integrates with your backend via a NoSQL-like API
- Fast Integration: Set up secure data protection in under 10 minutes
For credit-card tokenization or enterprise security features check out the Databunker Pro.
⚡ Why Databunker?
Databunker provides a robust, open-source vault that eliminates the false sense of security from traditional encryption methods, offering developers a practical way to protect sensitive data.
🚀 Deployment & Usage
- Self-Hosted: Run on your cloud or on-premises infrastructure
- Open-Source: Licensed under MIT for free commercial use
- GDPR Compliant: Meets modern privacy regulation requirements
- High Performance: Go-powered API ensures fast tokenization and data access
🔐 How It Works
- Store sensitive data in Databunker via API calls
- Receive UUID tokens to reference data securely in your application
- Query data using secure, hash-based indexing
- Benefit from built-in protections against injections and bulk data leaks
Get started with Databunker to secure your sensitive data efficiently.